The Executive Yuan yesterday strongly condemned cyberattacks suspected to have been launched by a pro-Russia hacking group the previous day targeting the Taiwan Stock Exchange (TWSE), the Directorate-General of Budget, Accounting and Statistics (DGBAS) and several local financial institutions.
It assured the public that government agencies are closely monitoring the situation and have a firm understanding of the incident.
In a statement, Cabinet spokesperson Michelle Lee (李慧芝) said that the Executive Yuan strongly condemned reckless hacking attacks on countries including Taiwan.
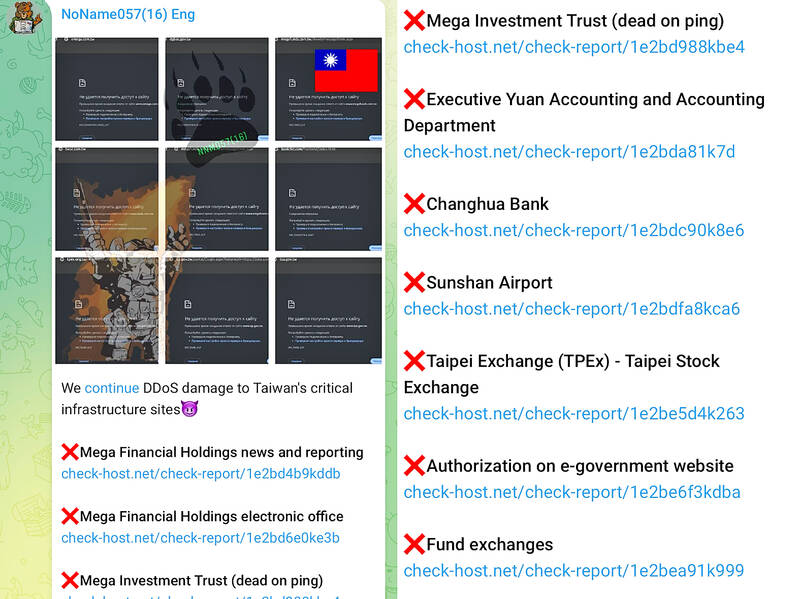
Photo courtesy of a reader
Vice Premier Cheng Li-chiun (鄭麗君), who also heads the National Information and Communication Security Task Force, has requested that the Administration of Cyber Security (ACS) gather information about the cyberattacks and help agencies make prompt responses, Lee said.
While the government would continue to monitor how the cyberattacks evolve, it has also informed all of the agencies under the central and local governments that they should work together to defend themselves from possible further attacks, Lee said.
The statement was issued after the Web sites of the TWSE, the DGBAS and several major government-invested Taiwanese banks, including Mega Financial Holding Co (兆豐金控), and Chang Hwa Commercial Bank (彰化銀行), crashed due to cyberattacks on Thursday.
NoName057, a pro-Russia hacker group, has claimed that it launched distributed denial of service (DDoS) attacks on Taiwan’s government agencies, financial firms and even Taipei International Airport (Songshan airport).
The ACS on Thursday confirmed that the attacks were made through DDoS, referring to a malicious attempt to disrupt the normal traffic of a targeted server, service or network by overwhelming the target or its surrounding infrastructure.
The TWSE said that at about 3pm on Thursday, it found that a large number of foreign Internet protocol addresses launched invalid queries on its network, causing unstable services for a short period.
The TWSE said its global Web site returned to normal at 3:22pm and saw no impact on its operations or the local stock market.
Mega Financial said the Web sites of the firm and its securities, commercial bill and securities investment trust subsidiaries were attacked on Thursday afternoon, but the networks returned to normal soon after their quick response.
NoName057 is the pro-Russian hacktivist group behind Project DDoSia, a DDoS attack toolkit that targets entities criticizing Russia’s invasion of Ukraine.
The Liberty Times (sister paper of the Taipei Times) on Tuesday cited cybersecurity firm Radware as saying that the attacks appeared to be retaliation for comments made by President William Lai (賴清德) on Sept. 1 suggesting China should have a territorial dispute with Russia.
“If it is really about territorial integrity, why don’t they [China] take back the land that was signed away and occupied by Russia in the Treaty of Aigun?” Lai asked.
The Treaty of Aigun, which was signed in 1858 between the Russian Empire and the Qing Dynasty, ceded about 600,000km2 of land in Manchuria to Russia.
The government is continuing to monitor the cyberattacks, which appear to have achieved little, but are showing no sign of stopping, Minister of Digital Affairs Huang Yen-nun (黃彥男) told the Liberty Times yesterday.
The Ministry of Digital Affairs has implemented strong countermeasures since China’s 2022 DDoS offensive during then-US House of Representatives speaker Nancy Pelosi’s visit to Taiwan, an official said on condition of anonymity.
These efforts significantly increased the resource costs of DDoS attacks, requiring hackers to outspend Taiwanese defenders 20:1 to achieve success, they said, adding that most Chinese attacks during the presidential election were neutralized.
Information technology experts speculated that the nation is preventing DDoS attacks by denying servers with foreign IP addresses from connecting to Taiwanese networks without limiting Taiwanese access to the Internet.
This method known as "flow cleaning" is a speedy and cost-effective counter to DDoS attacks, said Cha Shi-cho (查士朝), professor of informational security at the National Taiwan University of Science and Technology.
Hackers mainly utilize foreign-based servers to conduct DDoS attacks, which leaves a footprint that could be easily tracked and identified by government agencies or private security firms, he said.
DDoS is an old and simple, but costly method that requires the attacker to commit enormous resources for temporary results, he said, adding that there is little need for alarm if these attacks did not compromise systems.
However, if the attackers gained control of corporate networkers, they could use the latter as a springboard to launch further attacks, which would be more difficult and expensive to defend against, he said.
Additional reporting by Hsu Tzu-ling

AIR SUPPORT: The Ministry of National Defense thanked the US for the delivery, adding that it was an indicator of the White House’s commitment to the Taiwan Relations Act Deputy Minister of National Defense Po Horng-huei (柏鴻輝) and Representative to the US Alexander Yui on Friday attended a delivery ceremony for the first of Taiwan’s long-awaited 66 F-16C/D Block 70 jets at a Lockheed Martin Corp factory in Greenville, South Carolina. “We are so proud to be the global home of the F-16 and to support Taiwan’s air defense capabilities,” US Representative William Timmons wrote on X, alongside a photograph of Taiwanese and US officials at the event. The F-16C/D Block 70 jets Taiwan ordered have the same capabilities as aircraft that had been upgraded to F-16Vs. The batch of Lockheed Martin

GRIDLOCK: The National Fire Agency’s Special Search and Rescue team is on standby to travel to the countries to help out with the rescue effort A powerful earthquake rocked Myanmar and neighboring Thailand yesterday, killing at least three people in Bangkok and burying dozens when a high-rise building under construction collapsed. Footage shared on social media from Myanmar’s second-largest city showed widespread destruction, raising fears that many were trapped under the rubble or killed. The magnitude 7.7 earthquake, with an epicenter near Mandalay in Myanmar, struck at midday and was followed by a strong magnitude 6.4 aftershock. The extent of death, injury and destruction — especially in Myanmar, which is embroiled in a civil war and where information is tightly controlled at the best of times —

China's military today said it began joint army, navy and rocket force exercises around Taiwan to "serve as a stern warning and powerful deterrent against Taiwanese independence," calling President William Lai (賴清德) a "parasite." The exercises come after Lai called Beijing a "foreign hostile force" last month. More than 10 Chinese military ships approached close to Taiwan's 24 nautical mile (44.4km) contiguous zone this morning and Taiwan sent its own warships to respond, two senior Taiwanese officials said. Taiwan has not yet detected any live fire by the Chinese military so far, one of the officials said. The drills took place after US Secretary

THUGGISH BEHAVIOR: Encouraging people to report independence supporters is another intimidation tactic that threatens cross-strait peace, the state department said China setting up an online system for reporting “Taiwanese independence” advocates is an “irresponsible and reprehensible” act, a US government spokesperson said on Friday. “China’s call for private individuals to report on alleged ‘persecution or suppression’ by supposed ‘Taiwan independence henchmen and accomplices’ is irresponsible and reprehensible,” an unnamed US Department of State spokesperson told the Central News Agency in an e-mail. The move is part of Beijing’s “intimidation campaign” against Taiwan and its supporters, and is “threatening free speech around the world, destabilizing the Indo-Pacific region, and deliberately eroding the cross-strait status quo,” the spokesperson said. The Chinese Communist Party’s “threats